
If you have been paying attention to the United States news cycle within the last few years, you may have noticed that there seem to be an unusual number of headlines about cyber-attacks. According to a ZDNet article, “There have been a huge increase in the number of ransomware attacks over the course of 2020, with a seven-fold rise in cyberattack attempts.”
In fact, according to the HHS Cybersecurity Program, they discovered at least a 72% increase in ransomware over the last 12 months. (HHS Cybersecurity Program is an enterprise-wide information security and privacy program that was launched in the fiscal year 2003, to help protect HHS against potential Information Technology threats and vulnerabilities). These incidents have included the full file dumps, screenshots, and even samples of the data pieces being recorded and extracted.
The most infamous cyber-attack of the year came from the compromised Colonial Pipeline on April 29th, 2021. According to Charles Carmaka, the senior vice president at cybersecurity at the firm Mandiant, said the hackers gained entry through a Virtual Private Network account that was no longer in use of the time of the attack but still could be used to remotely to access the company’s computer networks. Charles continued to describe that the hack had originally traced a large of number of leaked passwords to the dark web but admits that investigators may never know for certain how the credentials were obtained.
Those of you unfamiliar with the Colonial Pipeline cyber-attack, on May 7th an employee in the Colonial Pipeline control room saw a ransom note that demanded a payment in cryptocurrency. The Operations Supervisor made the “exact right decision” to shut down the gasoline pipeline for the first time in its 57-year history. Since the company’s system “transports roughly 2.5 million barrels of fuel” to almost the entire east coast, it caused quite a few disruptions with long lines at gas stations, no fuel at many of them, and panic buying by consumers. As a tireless physical inspection of the gas pipeline occurred days and weeks after the note arrived, Colonial found no reason to believe that the pipeline was in danger of being damaged. Since the hackers threatened to release all 100GB of data, including their passwords, Colonial was forced to pay the ransom of 4.4 million dollars. Even though over 85% of the ransom was recovered in large part due to the FBI and the US government, the total cost to shut down operations, even for several days, almost doubled the cost of the original ransom.
Ransomware attackers are targeting the United States in alarming numbers and the colonial pipeline cyber-attack is the canary in the coal mine. Although the attacks seem to be targeting the core infrastructure of the United States including, education, healthcare, and Utilities (See the Fg.1 below), it is apparent that more than 55% of companies do not have the necessary tools, teams, or tests in place to fight a potential ransomware attack.
average-ransomware
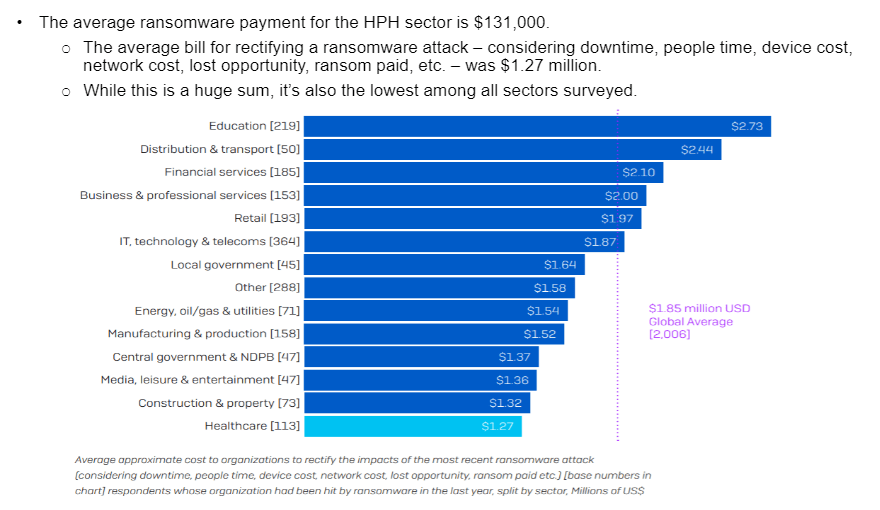
Of the most vulnerable business segments listed in the figure above, it should be noted that:
- Over 83% of Healthcare organizations are using Cloud services
- 90% of K-12 school districts are using cloud storage
- 88% of K-12 school districts are cloud-based software systems
- 71% of utility companies use cloud computing systems
Whether your data is on-premises, hybrid, or 100% in the cloud, it is more important than ever to adopt a well-architected framework as AWS has provided for its users. This framework focuses on 5 pillars (Operational Excellence, Security, Reliability, Performance Efficiency, and Cost Optimization) with security and operational excellence being at the top of their list.
To help avoid potential threats and attacks, AWS has provided a series of best practices that can help protect your companies’ data from falling into the wrong hands. Amazon recommends running well-architected reviews to address security risks and bolster any architectural deficiencies. This well-architected exercise is best performed with a Certified AWS Advanced Consulting Partner to catch what would otherwise be missed by going through the exercise alone.
As a Certified AWS Advanced Consulting Partner, we specialize in providing well-architected reviews, AWS cloud solutions, and AWS cloud consulting services. We understand the importance of having secure IT infrastructure, especially when it comes to protecting your organization from ransomware attacks. We provide a range of AWS Services Partner tier services, including risk assessment, security policies, and security architecture review and our team of experienced professionals have the knowledge and expertise to help you design and implement the best security protocols for your organization.
If security is at the top of your mind like it is for us, we would welcome you to reach out to our AWS team at Teqfocus to walk you through what a well-architected review would look like and how participating in one (even with a single workload) will increase your company’s security posture.

